The urgency for business leaders to understand network security types has never been greater. With cybercrime damages projected to reach $10.5 trillion annually by 2025, the stakes for protecting digital assets and ensuring business continuity are at an all-time high.
| As Shaun Hutchings, Chief Technology Officer for CCPlus Inc., states: “A tailored network security strategy not only defends against evolving threats, but also empowers teams to operate with greater confidence and efficiency.“ |
For small and mid-sized businesses, knowing which network security measures to deploy, and how to align them with organizational goals, can mean the difference between resilience and ongoing costly disruptions.
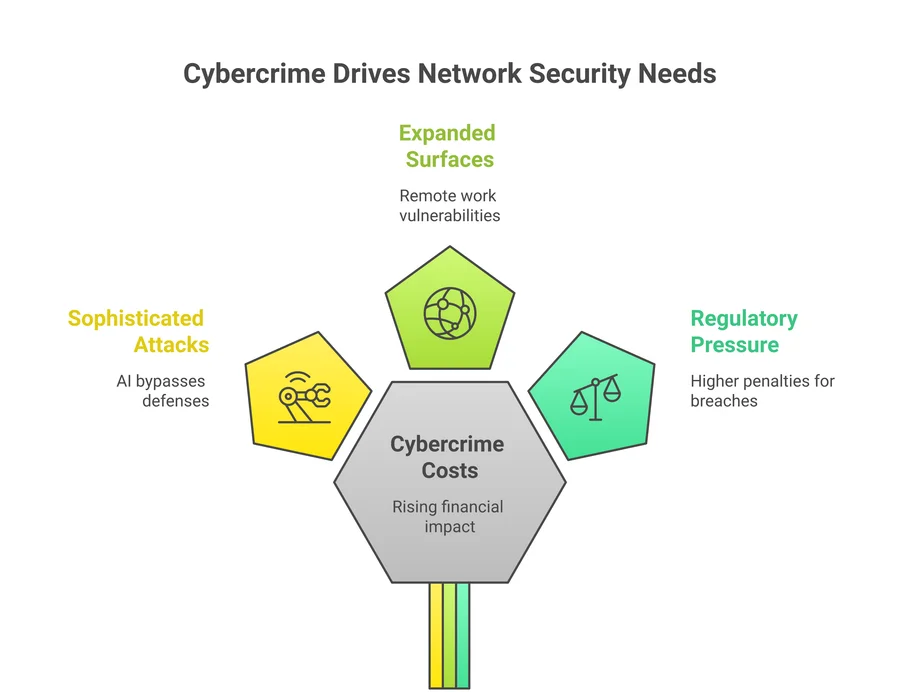
What’s Driving the Need for Network Security?
60% of small businesses say that cyber threats are a top concern. Beyond evolving cyber threats, SMB’s must ensure their networks are secure enough to be available to customers and users day and night.
Other examples of the mounting pressures related to network security include:
- Escalating cybercrime costs: The financial repercussions of breaches can be crippling, with even mid-sized companies exposed to risks that previously targeted only the largest enterprises.
- Increasing attack sophistication: Adversaries now exploit AI and automation, making traditional, static defenses insufficient.
- Hybrid and remote workforces: The shift to distributed teams expands the attack surface, requiring adaptive, context-aware controls.
- Regulatory pressure: Evolving compliance mandates introduce stricter requirements and steeper penalties for non-compliance.
Reflecting these realities, Gartner forecasts a 15% rise in global cybersecurity spending, as organizations increasingly seek value-driven partners for strategic network security guidance-not just off-the-shelf solutions. A certified, proactive team can help ensure your security investments align with business growth.
Understanding the Types of Network Security
Only 8% of organizations reach a mature stage in network security. Reaching a “mature” stage of network security is rare because the threat landscape is constantly shifting. Most organizations struggle not with awareness, but with the breadth of tools and expertise required to defend every layer of their environment.
The major categories of network security each serve a distinct role:
- Firewalls: Whether packet-filtering, stateful inspection, or proxy-based, firewalls act as the first checkpoint between internal systems and external traffic. They establish baseline rules to block unauthorized connections, limit exposure, and reduce the attack surface.
- Intrusion Detection and Prevention Systems (IDPS): By inspecting traffic in real time, IDPS tools identify malicious patterns such as brute force attempts, malware signatures, or abnormal traffic flows. Unlike traditional monitoring, prevention-capable systems can automatically block or contain these threats before they spread.
- Virtual Private Networks (VPNs): VPNs encrypt communications between users and the corporate network, protecting sensitive data from interception. They are especially critical for remote workers and distributed teams, where traffic frequently crosses unsecured networks like public Wi-Fi.
- Network Access Control (NAC): NAC ensures that only trusted users and devices can connect to the network. It verifies identity, device health, and compliance with security policies, automatically denying or restricting access if standards aren’t met — reducing the risk of infected or noncompliant devices introducing vulnerabilities.
- Security Information and Event Management (SIEM): SIEM platforms centralize log data from across the infrastructure — firewalls, servers, endpoints, and more — to provide visibility into suspicious activity. With correlation rules and alerting, SIEM enables faster incident detection and supports regulatory compliance through detailed reporting.
No single layer is enough. A firewall won’t stop a compromised laptop, and endpoint protection can’t see malicious traffic moving laterally across a network. Effective security comes from layering these defenses so they work together rather than in isolation.
The real challenge is choosing the right mix for your business environment. That requires more than technical know-how — it requires aligning controls with your organization’s goals, operations, and risk tolerance.
Scale Safely With Trusted Security
What Layering Network Security Types Look Like in Practice
A real-world incident often unfolds with little warning. Imagine a mid-sized company uncovering unauthorized access to sensitive data late on a Friday. Within minutes, layered network security controls activate: firewalls restrict suspicious connections, intrusion detection systems highlight anomalies, and endpoint protections isolate at-risk devices.
This coordinated response, directed by experienced IT professionals, not only limits the breach but also preserves business continuity. In fact, organizations adopting a layered approach have significantly reduced breaches, demonstrating the value of multiple, integrated types of network security.
Types of Network Security and Their Functions
| Type of Network Security | Primary Role in Defense | How It Works with Other Layers | Business Value |
| Firewalls | Gatekeeper at the perimeter and between network zones | Provide first-level filtering, feed traffic logs into SIEM for correlation | Reduces exposure by blocking unauthorized access early |
| Intrusion Detection and Prevention Systems (IDPS) | Real-time threat detection and blocking | Identify malicious activity that slips past firewalls; share alerts with SIEM | Limits damage by stopping attacks before they spread |
| Virtual Private Networks (VPNs) | Secure remote and cross-network communication | Protects data in transit; complements NAC by verifying remote user/device identity | Protects sensitive communications for remote workers and partners |
| Network Access Control (NAC) | Control who and what connects to the network | Works with endpoint security to deny infected or noncompliant devices | Prevents compromised devices from becoming entry points |
| Security Information and Event Management (SIEM) | Central visibility and response coordination | Correlates data from firewalls, IDPS, endpoints, and NAC for faster detection | Enables rapid incident response and supports compliance |
Understanding the Main Types of Encryption in Network Security
Encryption serves as a cornerstone of network security, ensuring that data remains confidential and trustworthy during transmission and storage. Today’s most prevalent encryption techniques include:
- Symmetric Encryption: Relies on a single secret key for both encrypting and decrypting data. While efficient, it demands careful handling and distribution of keys to prevent unauthorized access.
- Asymmetric Encryption: Utilizes a pair of keys-one public, one private-to secure communications and verify identities, making it ideal for secure exchanges over untrusted networks.
- Hashing: Converts information into a fixed-length string, safeguarding data integrity by detecting unauthorized alterations, though it cannot be reversed to reveal original content.
To stay ahead of evolving threats and maintain compliance, organizations must ensure their encryption protocols are continuously updated and professionally administered.
Exploring Types of Scanning in Network Security
A disciplined approach to network scanning is foundational for organizations intent on managing risk with precision. Effective scanning is not a one-size-fits-all exercise-it requires a blend of targeted techniques and ongoing vigilance. The main types include:
- Vulnerability Scanning: Proactively surfaces known software flaws and misconfigurations, forming the backbone of a strong defense.
- Port Scanning: Methodically maps open ports, identifying possible gateways for exploitation.
- Malware Scanning: Inspects files and traffic for malicious code, enabling rapid containment of threats.
- Configuration Scanning: Verifies that system settings align with security policies and regulatory obligations.
While automated tools accelerate detection, integrating human oversight with multiple scanning methods produces the most resilient results. This layered approach positions businesses to address both current and emerging threats before they escalate.
How Different Types of Network Security Deliver Tangible Business Value
Network security is not just a technical concern-it is a critical business enabler. The right mix of controls can mean the difference between resilience and disruption.
- Threat Prevention: Proactive measures are indispensable, especially when 60% of small businesses shut down within six months after a cyberattack.
- Regulatory Compliance: Encryption and access controls help organizations align with complex data privacy regulations.
- Operational Continuity: Segmentation and redundancy minimize downtime, sustaining productivity and service delivery.
- Data Protection: With 82% of breaches involving cloud-stored data, robust endpoint and cloud security become non-negotiable.
- User Trust and Reputation: Demonstrating strong security practices reassures clients and partners, enabling growth without sacrificing agility.
By taking a prescriptive, business-focused approach, leaders empower secure expansion and sustained trust.
| More articles you might like: |

Translating Network Security Insights into Meaningful Business Results
Translating network security insights into tangible business outcomes requires deliberate steps. Consider the following actions to keep your defenses effective and adaptive:
- Assess your current security posture: Regularly evaluate existing protections to pinpoint exposures.
- Prioritize proven solutions: Invest in established controls-firewalls, encryption, and active monitoring-to address core vulnerabilities.
- Engage with experts: Work with experienced partners to develop a holistic risk assessment and implementation plan.
- Stay current on threats and compliance: Monitor the evolving landscape so your controls remain relevant and robust.
| Discover Trusted Cybersecurity Services in Rochester, NY |
Contact CCPlus to discover how expertly managed, tailored network security, backed by decades of experience, 24/7 monitoring, and a trusted local helpdesk, can protect your business and support your operational goals. With us, IT doesn’t just run smoothly, it becomes a reliable partner that empowers your team, keeps your data safe, and helps your business grow with confidence.




Comments are closed.